Many developers now days Obfuscated or Confused the DEX files so that it becomes harder to reverse engineer them. Today, I will teach you how you can find methods within the class that are pointing to another class. Many apps are encrypted or obfuscated, the methods and classes have weird names so that we cannot know what does a specific method or class do. However, the main classes and methods of the app are sometimes not obfuscated and that way you can find interesting methods in the class pointing to different classes which we can modify.
In today’s tutorial we will be modding the FilmoraGo APK file, I will show you how you can mod the app to enable pro features, we will activate the pro subscription.
Requirements:
1) Basic knowledge on how to MOD application.
Let’s begin
1) Download FilmoraGo APK from Apkcombo.com or click here to download APK
2) Remove signature check because the app has a signature check, see our tutorial on how to bypass signature check.
3) Decompile it
4) In the example screenshot below, we can see that inside the com/filmorago/oversea/google/subscribe/SubscribeModel.smali there are many boolean methods called from g.smali (Lj3/g;>i()z and others) which is J3/g.smali class, so we can assume that it might be something related to the subscription within the app.

Let’s go to that class and make every boolean method true.
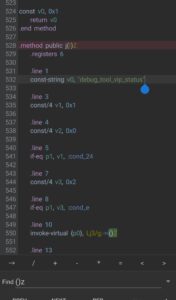
Inside g.smali I found this string related to the VIP Status, which I am assuming is related to the pro version. So I think we are looking at the right smali file, so let’s make everything TRUE
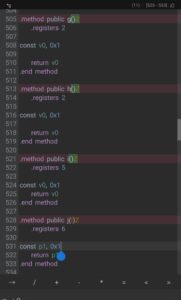
5) Let’s compile the APK file, sign it and test it to see whether we got the pro version or not.
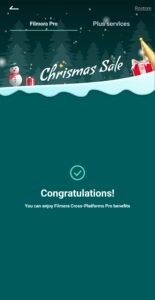
Wow, so it worked. We are now a PRO Member of FilmoraGo.
The application did not have their main classes Encrypted or Obfuscated, which allowed us to debug them. Whenever you are trying to MOD any application, try to find payment classes, subscription classes, IAP classes, etc. within the main classes of the app. You can find some interesting methods, also find strings and see what methods are being called near those strings.
As always, try modding different methods and see the results, you will only learn if you try.
